hey uh. did anyone else see that patreon fired all of their security staff. 😐 everyone change passwords, set up 2 factor authentification, and/or take your card info off of the site
It’s really not as alarming as it sounds – there’s a good thread about it all on hackernews I can’t be assed to go find again bc I’m already in bed but it should come up with a Google search. There’s a message in there grabbed from the CEO(I think?) Statement made in a specific discord.
Pretty much boils down to they’re working with another source. We don’t have the details why the team was fired (and it was a small team of 4 or 5 from what folks can find on LinkedIn) but I’m going out in a limb and saying they didn’t part on good terms. It’s pretty fuckin shitty of a security engineer to go on a social media and blast the company is potentially vulnerable. It’s one thing if that simply hurt Patreon, but a breech would significantly impact EVERYONE. That was a huge dick move, which leads me to believe it was done out of anger.
The MOST LIKELY scenario of what’s happening is Patreon is getting ready to go public and in order to do so they need to seriously beef up their security measures to prove to investors they’re airtight and trustworthy with all this money being handled. That means splurging on Very Expensive security firms that are outsourced, or curating a new team of their own with security engineers who are well known, highly trained and skilled, have worked with the big dogs, and are also very pricey. This isn’t too unusual to see when a startup finally gets off the ground. Very likely their current team just didn’t meet the standards expected in a publicly traded company. Probably didn’t break the news to that team in a very good way, or blindsided them.
However, until more details emerge we can only assume. But this isn’t a reason to panic. Patreon would land in some seriously deep shit if they were outright negligent like that. I guarantee you they already had another team – be it one they’re going to work with going forward or a temporary one – locked and loaded and ready to go before the team they let go was even out the door.
That said, thanks to the dick move announcement, people freaking out like they always do, and transitions always being a little sticky, it’s a good idea to at least enable 2FA if you haven’t already. Even in the highly unlikely event they did get breeched and hacked and your password revealed, that will prevent your account from being accessed. Also, card information is like, never stored on any sort of internal database anymore. It’s rarely ever even unencrypted or seen by a human for that matter. Annnd usually handled by a whole different API and sometimes several different payment processors. Not saying it’s impossible to get your card info in the event of a hack, but man the chances are like, ridiculously low to improbable.
It won’t hurt to take some extra precautions as you should anyway these days but until we have some actual facts about what went down, there’s 0 need to make any fuss. Twitter is already kinda doing that, sadly. Cyber security is way, way, WAY more intricate than the average Joe thinks it is, and when you’re working directly with financial institutions it is not something you take lightly, at all.
So this should not be panic-induing but this does NOT look good for Patreon.
You don’t really layoff an entire security team and then outsource if you want any sort of continuity of operations in the near term of the next 18 months or so.
(Some background, I’ve been working in computer security now for about a decade and a half: In research, then operations at an antivirus company, in the operations team of a networking company. If you’re in computers, you’ve heard of them.)
This is PURELY a take from the outside but it looks as if there was no real transition plan from an internal team to the outsourced security team. There’s a lot of institutional knowledge that exists in any sort of IT/SecOps/etc. team; the sort of things that nobody writes down because “everyone knows it.” That goes right out the window when you layoff all, or even large parts, of a team. Even the best of transition plans leave holes in knowledge that have to be re-learned or re-architected (I myself, have been asked for things i KNOW i’ve handed over after I’ve left.) There’s no transition plan that is perfect, but having no transition plan is the worst.
Furthermore, what Patreon announced publicly is at odds with what their former employees are saying:
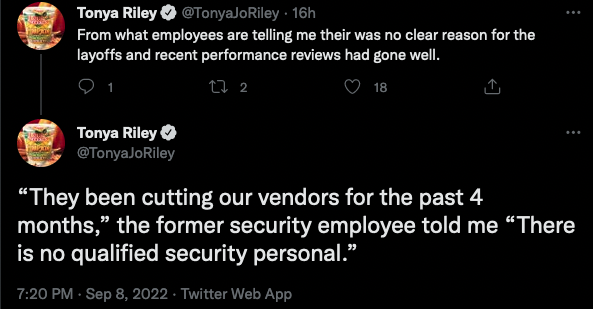
We don’t have the whole story but the bits we do have don’t exactly add up, so something seems to be going on, and people should rightly be concerned.
The trick is, about what?
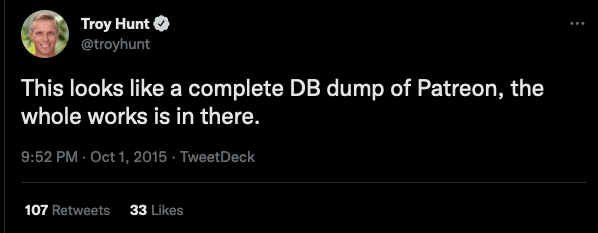
The easiest way to figure out what they COULD get is to look at the last time Patreon was breached, all the way back in 2015: They didn’t get credit card numbers, but they did manage to dump the entire Patreon database:
And yes that means DMs:
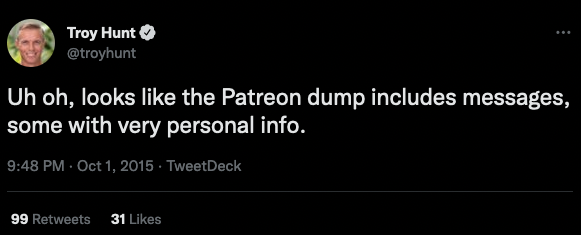
Personally, thats the more concerning of the threat models, especially when PayPal is an available option for paying Patreon.
My concern would be the personal, not public data (addresses, etc) that i keep in Patreon plus any sorts of sensitive DMs or anything in there. If you don’t have the list of your active subscriptions public, its not unreasonable to be concerned about that too in the event of a breach.
But all that being said: Just because a security team being laid off yesterday doesn’t mean its more likely they’re going to be breached today. The concern should be a forward looking one because:
1) The replacement is going to need time to transition, which means there’s a likely lack of oversight in policies and monitoring.
2) Management thought this was a good idea which sets the tone for security decisions being made in the future.